Notice: Important information regarding changes to the SafeLaw Application.
At the end of 2020 we implemented 10 new information security questions into the SafeLaw application. We have provided detailed explanations of each new question below, why they are important and how you might be able to make changes to your own internal information security protocols to implement them quickly. If you do not answer ALL the questions on the application we will be unable to provide your terms for Cyber Insurance.
SafeLaw New Application Question FAQ
Does the Applicant use multi-factor authentication for all remote access to the Applicant’s computer network?
What is Multi-Factor Authentication?
As discussed in question 3 above, MFA in computer networking is a security mechanism that requires an individual to provide two or more credentials in order to authenticate their identity and log into a computer. Usernames and passwords are the most commonly used access control elements of computer security, but also the most vulnerable. MFA requires an additional credential to log in such as a biometric identifier, specific location, or a security token. By now, most people in the United States have been exposed to MFA at some point, such as when you log into your bank account online and it asks to confirm your identity by calling or texting you a single use code to complete the login. MFA adds a strong layer of security to traditional passwords, which are typically vulnerable to brute force attacks or theft.
Why Is multifactor authentication important for remote access?
Although different types of remote access have different levels of exposure, permitting any kind of remote access to the firm’s computers creates a serious risk of attacks and catastrophic loss. Most firms use some kind of username and passwords to restrict access, but passwords are far too vulnerable to protect your firm. We are often asked why passwords are so vulnerable to attack. Although the answer is subject to regular debate, most experts agree that the main reasons passwords are vulnerable are as follows:
- Strength – The strength of a password lies in the hands of the users. Unfortunately, most users choose easy-to-remember words and phrases over unique strings of alphanumeric characters. Research from NordPass found that the average Internet user has somewhere between 70-80 passwords, which is probably the main reason why most users trade off strength for convenience.
- User Identification – Passwords don’t provide any information on the unique identity of the user. Passwords can be shared, used, and exploited by anyone who gets a hold of them.
- Security Awareness – Most users are not IT security experts and lack any understanding of how passwords are pilfered by threat actors. It’s very common for users to unknowingly give away their passwords through phishing attacks, man-in-the-middle attacks, and similar methods of farming login credentials and passwords.
- History – Passwords and password cracking is not new, not even close. For hundreds of years, various militaries, spy agencies, law enforcement bodies, private organizations, and enterprising criminals have been devising ways to crack passwords. Over time, many different methods and sophisticated tools and techniques have been developed to crack any password. In the past, cracking passwords could take days, weeks, or even months. With the computing power available today, passwords can be cracked in seconds, minutes, or hours. These are literally hundreds of automated tools and services created solely for the purpose of cracking passwords and these tools/services are inexpensive, easily accessible, and easy to use even for the novice threat actor.
According to Verizon’s 2019 Data Breach Investigations Report, 79% of hacking related breaches involved stolen credentials. This single staggering statistic shines a light on the fallible nature of humans and the utter failure in the security provided by passwords. It also underscores why your firm must deploy MFA to tighten their security, especially for remote access to the firm’s network. MFA isn’t infallible, but the additional layers of verification required by MFA means that even if one of the authentication factors is compromised or stolen, threat actors can’t obtain illegitimate access without the other authentication factors.
How can I ensure that our firm has MFA enabled?
If you are not certain that MFA is enabled at your firm, it is possible to determine if MFA is enabled within Office 365. The link below provides instructions on how to check, but the instructions are intended for IT experts, so please.
MFA is relatively easy for IT professionals to implement quickly at no additional cost to the firm. If you discover that your firm doesn’t use MFA for remote access, the following links provide fairly straightforward instructions on implementing MFA within Office 365 and Google Workspaces.
Google Workspaces – https://support.google.com/a/answer/9176657
Do you have a process in place to regularly download and install patches within 30 days of release on your computer network (including all hardware and software publicly accessible through the internet)?
What are patches?
With respect to computer software and hardware the term “patches” means application and software updates that improve the security, functionality, usability, or performance of a program. A patch management process refers to the process managing a network of computers by regularly implementing patches to fix vulnerabilities to keep computers up to date.
Why are patches/software updates important?
Software and hardware providers regularly find critical security flaws in their products that must be fixed to prevent security breaches including Ransomware attacks. According to the US-CERT Vulnerability Database, 17,447 vulnerabilities were documented in 2020, which is a new record and the fourth consecutive year with a record number of documented security flaws. Furthermore, nearly 60% of data breaches in the past two years can be traced back to a missing operating system patch or application patch, according to researchers at Automox.
Firms that support a bring your own device (“BYOD”) policy must also ensure that any computers and devices owned by employees and used for work are patched. Likewise, firms that permit remote access of any kind must patch any computers and devices with access to the firm’s network are patched. In both cases, the patching should be done just as regularly as company owned hardware.
Few threat actors have the resources and expertise necessary to discover new security vulnerabilities, so most choose to target known vulnerabilities. Therefore, once a patch is available, firms must install them as soon as possible before threat actors can exploit the vulnerability. Larger firms with large and/or complex systems may require time to test and install the patches on their computer equipment, especially complex patches that require system reboots. While this is understandable, patching is critical to keep threat actors out of the firm’s systems and secrets. Even a commitment to install patch updates once a week would significantly reduce the risks of Ransomware and hacking.
Firms frequently overlook some equipment when applying patches.
When we conducted the 2020 SafeLaw claims analysis, we were not surprised to discover that a high percentage of claims arose out of the firm’s failure to install patches in a timely manner. Despite the evidence and the warnings, it is still somewhat common for firms to overlook patching for weeks or even months in some cases. However, we were shocked to discover that several large Ransomware claims arose out of vulnerabilities in equipment that hadn’t been patched for years or were never patched once. Upon interviewing numerous firms, we discovered that it’s common for firms to overlook certain types of equipment when applying patches. The equipment that firms commonly neglect to patch are as follows:
- Internet Modems – A firm’s network connection to the outside world is critically important to protect, but in our experience many firms do not patch their modems at all. In several of the Ransomware claims we adjusted; threat actors targeted vulnerabilities in modems that were published more than 12 months before the attack. Most of the firms we spoke to about this issue said they thought that modems were updated automatically, either by the manufacturer or by the Internet service provider (“ISP”), but it is only true sometimes. If your firm rents or leases a modem from their ISP, then it’s likely that the ISO update the software on the modem regularly as part of the rental charge. However, if you bought your router (common as we all like to save money), then you a responsible for updating it.
- Firewalls – Firewalls are often the first line of defense against threat actors. For this reason, keeping your firm’s firewalls up to date is extremely important. Cybersecurity experts project that firewall performance can be less than 50% effective without proper patching and the failure to properly patch firewalls is a leading cause of firewall failure. With that in mind, we were surprised to discover that many firms neglect to patch their firewalls. In reality, firewalls need to be updated the minute you remove them from the box, so we asked why firms don’t patch firewalls as frequently as they do everything else? The most common response we received is that many firms assumed that all firewalls are patched automatically by the manufacturer, which is not correct. Secondly, a shockingly high percentage of firm’s we spoke to view firewalls as disposable equipment, which require replacement every 3 years, but do not require updates. The IT expert at one firm stated that firewalls are only effective until a new version becomes available. He also said that all of the important security updates and features are only incorporated into the new firewalls and so it isn’t worth updating older firewalls. While it is true that new firewalls tend to receive new features that are not made available in older models, every firewall manufacturer we looked at publishes critical security patches. In addition, security experts recommend that firms check for firewall updates every single day.
Does my firm already have a patch management process?
If you either outsource your IT management to an outside firm, or have a dedicated IT professional on staff, most likely they have a “patching procedure” and if you ask them, they should be able to confirm what their procedures are and how frequently they are performed. If you find that your firm doesn’t already have a patch management process, then you should implement one as soon as possible. If confidentiality or privacy is a critical part of your business, then patch management is mission critical.
If your firm lacks IT support, you can use a manual or automated patch management process. The best approach to patching often depends on your IT expertise as well as the size and/or complexity of your computer network. Dedicated patch management software makes the process of managing and updating software easier by allowing the user to scan multiple software applications for updates, identify missing patches, and install the latest updates. A link to several highly rated patch management software products follows below:
Are all systems and data on your computer network backed up at least weekly?
What are computer system backups?
Generally speaking, system backups are a copy of computer data taken and stored elsewhere so that it can be used to restore the original data if it is corrupted, destroyed, or unusable. Not all backups are the same or as effective and many firms discover this important fact too late! At a high level, there are three basic types of backups, which are as follows:
- Full backup – A full backup is the process of copying all data to another location. This type of backup is the most basic type of backups. Although full backups require the most resources and take much longer to execute than other types of backups, they are also the most comprehensive type of backup, require the least time to restore, and are usually the most reliable.
- Incremental backup – An incremental backup starts with a full backup and then only backs up the data that has changed since the last backup occurred. Each backup builds upon the last backup and since only the new and changed data is backed up, incremental backups require fewer resources and can be completed quickly. However, restoring your system from incremental backups requires the piecing together of data from multiple backup sets, which usually results in the slowest data recovery time and are less reliable.
- Differential backup – A differential backup is similar to an incremental backup. It only backs up new or changed data. However, with a differential backup, all files created or changed since the last full backup are backed up each time a differential backup is performed. Differential backups are faster to perform than full backups and restoring from a differential backup is faster than restoring from an incremental backup. However, performing differential backups typically require more resources than incremental backups and restoring from a differential backup is typically slower and less accurate than restoring from a fill backup.
Why backups are important?
The purpose of backups are to create a copies of data that can be recovered in the event the original data becomes corrupted, destroyed, or unusable. Data loss can result from accidents, hardware or software failure, or computer attacks such as Ransomware. Backups allow the firm to restore important data and reduce the interruption of business operations after an unplanned event.
It is also worth noting that even in the best cases, Ransomware infections typically result in a loss of 10%-20% of the firm’s data, so if the firm elects to pay the ransom and the threat actors provide valid decryption keys firms still need to rely on backups. Failure to create reliable backups can result in catastrophic loss including ransom payments, forensic expense, data restoration costs, loss of billable hours, loss of clients and legal liability from lawsuits and regulatory inquiries. Ultimately, reliable backups can save your firm.
How often should I back up my computer network?
By now, everyone with a computer should know that backups are important, so theoretically no one should have to pay off Ransomware extortionists. However, the headlines are full of reports about Ransomware victims in every industry that should have had top tier backup strategies. So, what’s the problem? Sadly, the answer is that far too many businesses don’t realize the value of having a reliable backup regimen until it is too late. Once firm’s are faced with mission critical data that can’t ever be recovered, the importance of having a backup becomes all too real.
The only way to protect a business against valuable data loss is by creating reliable backups regularly. Important files should at least once a week, and once a day is highly recommended. Depending on the timing and circumstances, losing a weeks’ worth of data can be devastating for a law firm. Ideally, your firm backs up data often enough the firm can immediately restore the computer systems after a disaster like nothing ever happened. Working with together your IT resource to set a recovery time objective (“RTO”) and a recovery point objective (“RPO”) are big, big parts of making that happen.
RTO refers to the amount of time the firm’s critical systems can be down without causing significant harm to your firm. Simply put, RTO is the amount of time your firm’s system can be down before the firm begins to suffer a significant loss of billable hours, missed deadlines, reputational injury, and similar issues. On the other hand, RPO refers to the firm’s tolerance for loss of data. Said another way, RPO refers to the amount of data the firm can lose before significant loss occurs. Unfortunately, there are no once size fits all RTO or RPO. Every firm is different, so in order to select the optimal RTO and RPO for your firm, you need to work with your IT resources and determine exactly how much loss the firm can sustain before you reach the point of no return.
How should we implement a backup plan?
No matter how big or small your firm is, a successful recovery after a disaster starts with creating a backup plan and committing to it. The backup plan doesn’t have to be time consuming or complicated to work, but there are some very important steps that need to be made to ensure the plan will go as planned when you need it most. Here are a few things you need to think about.
- Organize Your Files – Begin by taking an assessment of your computer system and identify everything you need to back up. Then organize your important files into well-named folders, so you can be sure that you’re backing up the necessary files and will be able to locate them during a restoration.
- Determine Backup and Retention Schedule – After setting the optimal RTO and RPO for the firm, determine how often must backup each data set to achieve your objectives. After determining the frequency at which you need to backup each data set, determine the data retention schedule in accordance with best practices and the industry’s data retention standards and requirements.
- Select Backup Location – There are many backup options to choose from depending on your firm’s needs, but at a high level firm’s frequently weigh the advantages and disadvantages of physical backups and cloud based plans. Physical data backup does give you more control than a cloud-based plan and recovery time is often faster than with a cloud-based model. However, physical data storage is typically more expensive and time consuming because as well because you will be responsible for managing, changing, logging, handling, and storing the physical media. In addition, physical media backups have a higher rate of failure than could based plans.
When selecting a location for your firm’s backups the most important thing is to ensure the backup isn’t stored on the same computer or network. Backups are useless if they reside on the same computer or network that gets infected by Ransomware or malware. Getting backup copies of data off the network you’re backing up with ensure the backups will remain viable even if the firm’s network is compromised. Ideally, your firm’s critical data will always be backed up to an offsite location that is not likely to be impacted by events at the primary location. - Execute the Backup Plan – Prevent computer system downtime and loss of the firm’s critical data by ensuring backups and completed on schedule. It’s also important to ensure the backups are completed successfully and that you are informed if one or more backups fails.
- Secure Backups – Regardless of the backup solution and location your firm selects, it is important to secure and restrict access to the backups. Protecting backups with secure file transfer and encryption will firm’s data retains its integrity. Also, restricting access to the backups will reduce the number of points of attack available to threat actors and minimizes the chances of the firm’s critical data is stolen, destroyed, or infected by Ransomware or malware.
- Test Backups – Much like everything else in life, no backup solution is 100% perfect, even under optimal conditions. Unfortunately, most people learn that backups are less than perfect under much less than optimal conditions. Therefore, performing regular tests of your backups is essential to surviving a disaster. For most firms, a system failure, data breach, Ransomware infection, and similar events are a disaster, and a disaster can quickly become a catastrophe if it isn’t handled well. Implementing regular system recovery tests is akin to any type of disaster response drill. Your objective is to implement, practice, and reinforce the steps taken during a disaster so that it doesn’t end up being a catastrophe. Inexplicably, many companies fail to do so—causing panic and chaos when disaster strikes and resulting in losses that are far worse than they should have been. Test your backups. End of story!
Do it Yourself Cloud Backup Solutions
If your firm lacks IT resources, a do it yourself (“DIY”) backup solution may be a good option to protect your files. There are plenty of inexpensive DIY backup solutions to protect your files. However, before you jump into anything it is important to understand that many DIY solutions are limited to file backups, which means it will only backup your audio, video, presentation, spreadsheet, word processing, and similar files. Many DIY backup solutions will not back up the firm’s applications and databases, such as accounting/billing, case management, practice management, and similar systems. Those programs may need their own backup solution. The right solution for your firm will depend on your needs, but we’ve listed a several popular DIY file backup solutions to help you start researching the best option for your firm:
- Windows 10’s integrated Backup and Restore feature— Windows 10 includes an integrated backup solution that allows you to create a full system image or even create a repair disk for when Windows inevitably goes bad. This free solution can be found by navigating to the Start Menu > Settings > Update & Security > Backup.
- BackBlaze – https://www.backblaze.com/business-backup.html
- iDrive – https://www.idrive.com/online-backup-security
- Crash Plan – https://www.crashplan.com/en-us/
- SpiderOak – https://spideroak.com/one/
- Acronis – https://www.acronis.com/en-us/solutions/business/#a_tab_2_1
- Carbonite – https://www.carbonite.com/products/carbonite-safe-for-small-business
Many of the service providers listed above provide for encrypted backups and secure file transfer. If you don’t currently backup, these platforms are simple, in many cases, push button systems to back up your data
Are backups kept fully isolated from your network in an offline, air gapped or cloud based storage, so that they are not accessible from the rest of your computer network?
Why is it important to isolate computer system backups?
Keeping a backup copy of critical data is a great way of reducing the losses from a Ransomware attack. However, that backup data isn’t much good if it’s also infected with Ransomware because it was connected to the network when the attack took place. Simply put, backups stored on the same computer or computer network become totally worthless if the computer or network is infected by Ransomware or malware. That is why it is important to store backups in a separate location from the computer or computer network being backed up. Storing backup copies separately from the computer network being backed up with ensure the backups will remain viable even if the firm’s network is compromised.
Physical backups segregated from the firm’s computer network and stored in an offsite location are considered the safest and most reliable backup solution. However, cloud based backup solutions can also provide your firm with reliable isolated backups, but only if done correctly. The problem with online storage is they sync with local data storage, so any Ransomware or malware infections that occur on your computer will be synced into the cloud storage shortly thereafter. For example, a file sync solution like DropBox or OneDrive allows you to work on your files locally and syncs the changes to cloud storage, so when a Ransomware attack occurs and encrypts/locks the data on your computer, DropBox or OneDrive will sync the infected (changes) data to the cloud copy as well. Many people believe that file syncing services such as OneDrive or DropBox are a good backup solutions, but they are not. In fact, the Dropbox disclaimers clearly state that DropBox was not even designed to be a backup solution. So, what is the right answer for your firm’s backup plan? As usual, there is not a perfect answer, but there are a few best practices that will protect your firm. With that in mind, we’ve outlined a few basic principles of for creating and storing reliable backups:
- Physical Backups – Done correctly, physical backup solutions are still the best single approach reliable backups. However, protecting your firm from Ransomware and malware infections requires that physical backups are “air-gapped” from the firm’s computer network. An air-gapped backup means that at least one complete backup of the firm’s data remains offline at all times and is not connected to any other network or the internet. The only way the firm’s data can be transferred into an air-gapped backup is by physically connecting some sort of removable device. If the firm’s backup has no connection to the network or Internet, it can’t be remotely hacked, corrupted, or infected with Ransomware or malware. In addition to physical separation, here are a few tips for physical backup strategies.
- Store Backups Offsite – In addition to keeping physical backups air-gapped, at your firm’s critical data should always be backed up to an offsite location that is not likely to be impacted by events at the primary location.
- Keep Multiple Copies – The more backups your firm has, the less risk there is of losing data. Your firm should keep at least three copies of their data. That way, if one copy be lost due to Ransomware, theft, system failure or natural disaster, there will be other copies to fall back on.
- Diversify Storage – On a long enough timeline all storage devices fail. Diversifying storage media minimizes the risk of backups failing at the same time. Use at least two different types of storage media when creating backups of your firm’s data.
- Cloud Backups – First, and most importantly cloud storage and cloud backup services are different, so don’t get the two mixed up. Cloud storage services are designed to do just that – store files. Cloud storage service tend not to offer features to protect your firm from Ransomware and they usually don’t backup your file system structure, which means that you will have to manually organize the data if you must restore from backup. A cloud backup service is what you want. Cloud backup services are specifically designed for disaster recovery, allow you to retain your file system structure, offer some protection from malware and Ransomware, and typically include security features, such as encryption and secure data transfer. When it comes to protecting your firm from Ransomware and malware, cloud backup services are the superior option.
- Most, if not all, cloud backup solutions will protect your firm’s data from hardware failure, power failures, or natural disasters, but it’s important to understand that most cloud backup solutions will not automatically protect your firm against malware or Ransomware. Cloud backups are usually vulnerable on two fronts: through connections to customer networks, and because it is shared infrastructure (ask any Solar Winds client). The good news is that many cloud backup providers offer “versioning”, which means that multiple copies of your files are saved over time, so if Ransomware strikes, you can restore the firm’s system from the most recent version of the backup before the infection. The bad news is that not all cloud backup services have versioning available. Even cloud backup services that do offer versioning often require it to be turned on first, so we highly recommend that you verify that your cloud backup service provider offers versioning and it is turned on for your firm’s backups.
- Hybrid Backups – The ideal backup plan strategy incorporates a combination of cloud and physical backups. By using both together, your firm can have:
- greater flexibility and control over the backup plan;
- the capability to create faster backups with fewer resources;
- the ability to restore the firm’s computer systems sooner after a disaster; and
- maximum protection against malware and Ransomware,
- Hybrid backups generally require the most planning and expertise. However, the combination of physical and cloud backup solutions can provide your firm with a flexible, cost-effective and secure backup strategy that will protect your data when disasters occur.
Do It Yourself Cloud Backup Solutions
If your firm is lacks IT resources, a DIY cloud backup solution may be the best choice for your firm. There are several inexpensive cloud backup solutions you can implement yourself in a few hours or less. However, before selecting a solution, it’s important to understand that many DIY cloud backup solutions are limited to file backups only, which means it will only backup your audio, video, document, spreadsheet, presentation, and similar files, but note firm’s databases and applications such as accounting/billing, case management, practice management, and similar systems. If you need to back up an entire system including applications, then selecting the right backup service is essential. We’ve listed several few popular DIY backup solutions including some that offer file backup and others that offer full backups that will allow you to restore an entire system quickly following a disaster.
- Windows 10’s Integrated Backup and Restore feature— Windows 10 includes an integrated physical backup solution that allows you to create a full system image and a repair disk for when Windows fails. This free solution supports physical and cloud backups. Windows Integrated Backup and Restore can be found on any Windows 10 machine by navigating as follows: Start Menu > Settings > Update & Security > Backup.
- BackBlaze – https://www.backblaze.com/business-backup.html
- iDrive – https://www.idrive.com/online-backup-security
- Crash Plan – https://www.crashplan.com/en-us/
- SpiderOak – https://spideroak.com/one/
- Acronis – https://www.acronis.com/en-us/solutions/business/#a_tab_2_1
- Carbonite – https://www.carbonite.com/products/carbonite-safe-for-small-business
Many of the service providers listed above provide for encrypted backups and secure file transfer and some even offer versioning. If you don’t currently backup, these platforms are simple, in many cases, push button systems to back up your data
Does the Applicant exclusively run supported operating systems on the Applicant’s computer network?
Why is unsupported software a problem?
Just about every product has a limited support lifespan and software is no exception. Operating systems and applications typically have specific end-of-life (“EOL”) date, which is announced by the developer later in the software’s lifecycle. The EOL date is point in time when the developer will cease to update and support that software. Once the end-of-life date has passed, will no longer be supported, meaning the developer will not provide technical assistance, bug fixes, updates, or security patches. The software will continue to work to an extent, but it will no longer be updated. Simply put, you’re completely on your own when using unsupported software.
Any computer or network with unsupported software is at risk. Unsupported software is much less likely to work with new hardware and software. In addition, unsupported software is significantly more vulnerable to malware, ransomware attacks, and data breaches, especially with respect to vulnerabilities discovered after the EOL date because they will never be fixed. These sorts of vulnerabilities are referred to as “forever day” vulnerabilities because even though the vulnerability may be public and the vendor may be aware of it, the unsupported software will never be fixed and therefore will be vulnerable forever. With that in mind, it’s not difficult to understand why threat actors make a living targeting firms with unsupported software. In short, it provides threat actors with a large pool of businesses with an attractive and easy to access back door to their computer system. For example, the WannaCry Ransomware, which infected tens of thousands of businesses in over 150 countries, specifically targeted unsupported Windows operating systems.
Unsupported software also raises potential compliance issues under domestic and international law. For example, failing to have up to date software may considered negligence under the General Data Protection Regulation (GDPR”). This means that if your firm has unsupported software and suffer a Ransomware attack or related security breach, the firm could be subject to the cost complying with an Information Commissioners Office investigation, defense expense, and fines and penalties levied under GDPR (or a host of other information security and privacy regulations).
How do I know if my firm uses unsupported software?
For the most part, it’s relatively easy to determine if the software your firm’s is using is still supported. Start by taking an inventory of the applications and operating systems used by your firm. Then check the status of each application or operating system on the developer’s or reseller’s website or just contact the developer for help. If the software is identified as “no longer supported by the vendor”, then it is unsupported. With respect to Microsoft products, the end-of-life date for Microsoft Windows 7 and Microsoft Windows Server 2008 was January 14, 2020. Microsoft is no longer providing updates or security patches to this software. Older operation systems have not been supported for several years. Please see the link below to Microsoft’s Lifecycle page, which lists the Microsoft software products that are no longer supported:
https://docs.microsoft.com/en-us/lifecycle/end-of-support/end-of-support-2020
What can you do if your firm uses unsupported software?
When it comes time to move on from unsupported legacy software, the firm must decide of the software will be decommissioned, upgraded, replaced, or used in isolation from the firm’s computer network. Sometimes replacing unsupported software is as simple as upgrading to the most recent version from the same vendor, but in other cases it can be complicated with far reaching implications especially when the unsupported software is a unique operating system with several obsolete applications that depend on it and a lot of underlying data. The operating system is the backbone of a computer. It manages all the communications between the computer hardware and it’s ecosystem including the applications, user interface, and peripherals. Replacing an entire operating system may impact the applications and peripherals that rely on it, so firms must tread carefully when selecting about unsupported software. With that in mind, here a few points for firms to consider when considering what to do with unsupported software.
- Upgrade – When circumstances permit the firm to upgrade the unsupported software to the current version, it is usually the most cost-effective option with the fewest problems. Upgrades are not optimal for every situation, but they typically suffer from the fewest issues with system integration, compatibility, functionality, and staff training, so when they are available upgrades are usually a good first choice for most firms.
- Replace – There are many cases when firms may choose to replace unsupported software with software that performs the same or similar functions. Replacing unsupported software may present additional issues system integration and compatibility, especially when the unsupported software is replaced by software from a different developer. However, with some exceptions for niche or specialized software, replacing unsupported software is considered relatively low risk.
- Decommission – In situations where the unsupported software is redundant or obsolete, firms may decide to decommission the software while retaining access to the historical data. Decommissioning aka “retiring” an application usually involves migrating data from the unsupported software to different software or another data repository or that can be accessed independently.
- Isolate and Protect – In rare cases, a firm may be required to retain highly specialized unsupported software to provide infrequent or sporadic access to data for regulatory or business purposes. In such cases, the firm should consider removing it from the network to minimize the risk of attack. Furthermore, if Internet connectivity is not essential for the functionality, keep the unsupported software segregated and air-gapped from the Internet also.
Do you scan and filter emails for malicious attachments?
What is email scanning and filtering?
Email scanning and filtering software automatically analyzes incoming email messages by assessing the likelihood that the emails are either legitimate messages or messages that should be quarantined such as spam emails or fraudulent emails such as phishing attempts and emails with malicious software code such as Ransomware. Spam emails are typically just a minor annoyance because they are unsolicited advertisements, but they don’t necessarily represent a threat. Phishing emails pose much greater danger to the security of the firm because they are designed to trick the recipient into: (a) installing malicious software code; or (b) revealing sensitive information such as personally identifiable information, passwords, or other confidential information. For example, many phishing emails frighten the recipient into clicking on a fraudulent link or opening a malicious attachment by feigning a breach or security problem.
Email scanning and filtering tools automatically analyze incoming emails and classifies them into categories such as spam, malware, adult, virus, impostor, or suspicious links. With email scanning and filtering technology, organizations can identify and quarantine emails that contain malicious software code, spam, phishing attempts, and fraudulent hyperlinks that may be part of a Ransomware attack before users can open them, click on fraudulent links or download Ransomware.
Why is email scanning and filtering emails important?
The majority of successful of Ransomware attacks begin with an email and the success of the attack depends on tricking a user into clicking on a fraudulent link or opening an attachment with malicious code. Training and educating employees about email-based Ransomware attacks reduces the amount of successful Ransomware attacks by a material percentage and the numbers are somewhat encouraging. However, humans are notoriously unreliable security gatekeepers and human error remains the number one source of all computer security breaches, including Ransomware attacks. Ultimately, no amount of employee training alone has been successful in stemming the tide of computer security breaches caused by human error.
Email filtering and scanning provides a quick yet dependable guard against malware and Ransomware attacks by removing the human element from the equation. By automatically scanning the email and quarantining emails that may contain malicious software code, phishing attempts, or fraudulent hyperlinks before users ever see them, firms can avoid the root cause of Ransomware infections and significantly reduce the probability of successful Ransomware attacks.
Your firm may already use email scanning and filtering.
Many email services already include basic email scanning and filtering as part of their email service bundles. For example, the two most popular email platforms for law firms, Microsoft 365 and Google Workspace, typically include a basic form of email scanning and filtering in most of their business email, and in many cases, the email scanning and filtering is turned on by default. Although the basic email filtering and scanning provided by Office 365 or Google are by no means the gold standard of Ransomware prevention, they provide basic protection against Ransomware attacks.
Some of the upscale business email bundles offered by Google or Microsoft provide more advanced protection at pricing accessible to any small business. For example, Microsoft incorporates “Microsoft Defender for Office 365” in their “Office 365 Premium” bundle, which is only $20.00 per user, per month. Microsoft Defender for Office 365 offers advanced and configurable threat protection such as sophisticated threats hidden in email attachments and links, endpoint management, and advance Ransomware and malware protection. Please see Figure 1 below for Office 356 Premium details and pricing:
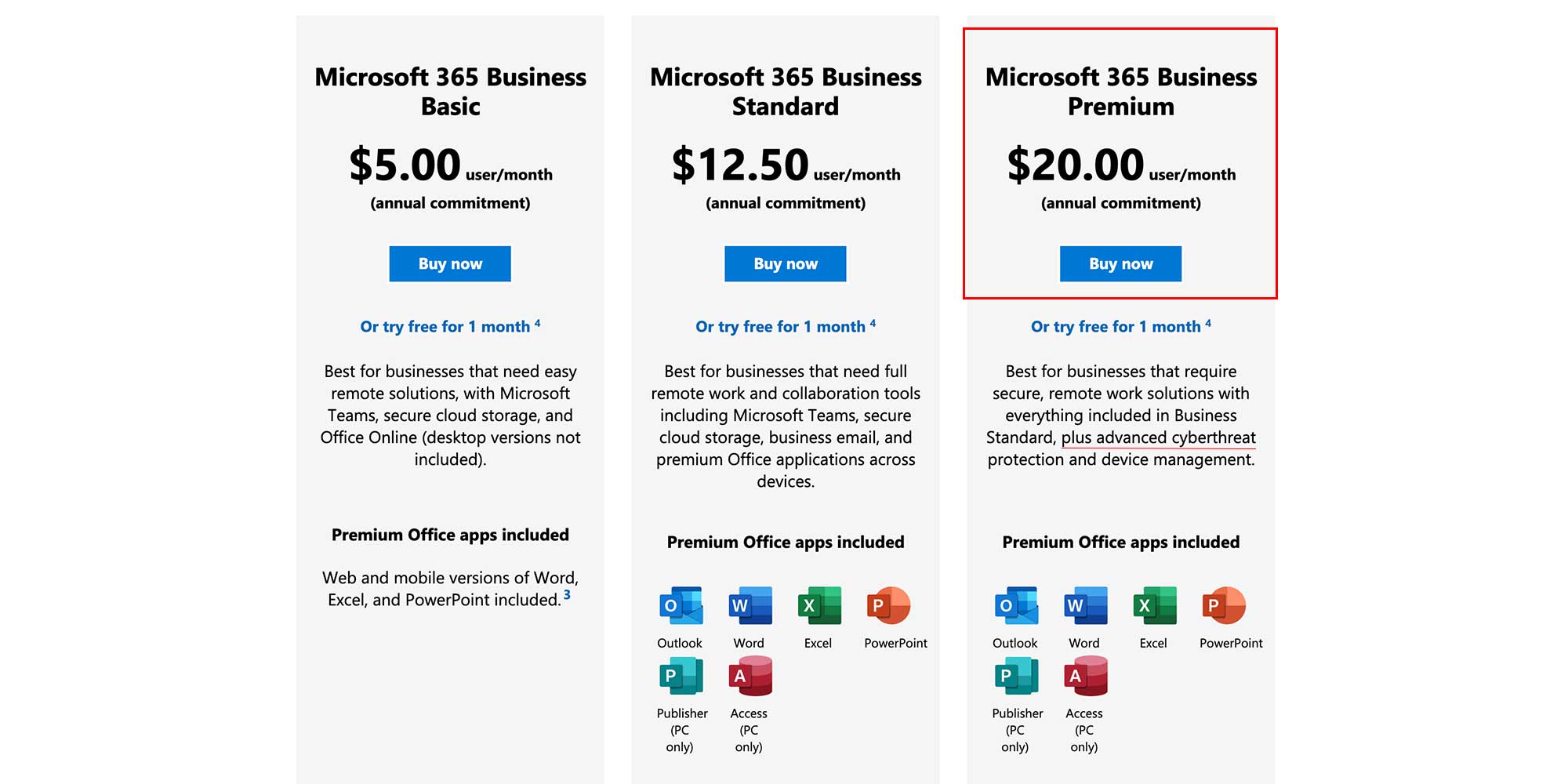
Google Workspaces has similar advanced security offerings. The “Business Plus” and “Enterprise” Plans both offer include enhanced protection. Please see Figure 2 below for Google Workspaces details and pricing:

Do you need help understanding or implementing email filtering and scanning?
If you have a dedicated IT service or outsource your IT services, your IT provider can tell you if your firm is using email scanning and filtering. Many outsourced providers have comprehensive experience responding to questions on cyber risk applications and can easily determine if the email bundle used by your firm includes basic email filtering and scanning. However, if your firm is using another email provider you will have to reach out to your IT service provider to determine if email filtering and scanning implemented.
If you don’t have an IT service provider and are managing your own email service and you’re using Microsoft 365 or Google Workspace, the links below can help you understand what is included in the email bundle you currently purchase.
https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/?view=o365-worldwide
https://support.google.com/a/topic/9974692?hl=en&ref_topic=2683824
In the event you are struggling to answer this question, please contact your broker for help. We can schedule a free call with an IT security expert at Secure IT 360 to help you answer one or more of the questions on your application.
Do you use DKIM, SPF or DMARC to authenticate your email?
What is DKIM, SPF, and DMARC?
Sender Policy Framework (“SPF”), Domain Keys Identified Email (“DKIM”) and Domain-based Message Authentication, Reporting, and Conformance (“DMARC”) are different tools that help authenticate email sent from your firm and protect your firm’s email domain from being used in business email compromise attacks, phishing emails, email scams, and other computer attacks.
Email authentication helps prove that emails sent from your email domain are not forged. For the sake of clarity, an email domain is the part of an email address that comes after the @ symbol. For example, the email domain for my email address, mikel@bigdatainsure.com, is “bigdatainsure.com”. Email authentication authenticates emails sent from your firm’s email domain, so the recipients email system can determine if email from your firm’s email domain is authentic. DKIM, SPF, and DMARC all work differently and provide a unique type of email authentication. However, they can also work together to affirm that emails sent by members of your firm are legitimate, that their identity has not been compromised, and that they are not sending email on behalf of someone else, which helps prevent your firm’s email from being spoofed and ensures that emails sent by your firm do get delivered instead of rejected or intentionally delayed. The bullet points below provide a short summary of SPF, DKIM, and DMARC:
Sender Policy Framework (SPF): SPF restricts who can send emails from your domain. It specifies which Internet Protocol (“IP”) addresses and/or servers are allowed to send email from your firm’s domain. If your firm uses SPF, the recipient’s email service will be able to verify the email is coming from your firm and not an imposter pretending to be you.
Domain Keys Identified Mail (DKIM): DKIM is another method email authentication technique that allows the recipient to check that an email was indeed sent by your firm. This is done by giving the email a digital signature and is securing it with encryption. DKIM also allows the recipient’s email system to verify that the content of emails from your firm haven’t been tampered with or compromised.
Domain-based Message Authentication, Reporting and Conformance (DMARC) DMARC combines the email authentication techniques from SPF and DKIM into a single framework and adds a reporting function as well. The reporting function provided by DMARC helps your firm gain insight in who is sending email through the firm’s email domain and informs you of any phishing or malware attempts to your domain. In addition, DMARC determines if email that fails an authentication check will be delivered, quarantined or rejected. In short, DMARC acts as an email gatekeeper and can prevent phishing and malware attacks.
Why is email authentication important?
One common method threat actors use to steal from business and consumers is by spoofing a legitimate company’s email and using it to commit phishing attacks, social engineering scams, or Ransomware attacks, or phishing. Threat actors frequently spoof members of a firm’s senior management and then send emails to lower-level employees or other members of senior management with urgent requests. In such cases, employees receive an urgent email from senior management and typically follow the instructions without question resulting in Ransomware infections, fraudulent funds transfers, or data theft. Likewise, threat actors will spoof a legitimate firm’s email and contact vendors or customers with urgent requests and in such situations the receiving party will frequently respond to the request quickly and without question resulting in significant losses.
Email authentication such as SPF, DKIM, and DMARC helps prevent your firm’s email domain being used in business email compromise attacks, phishing emails, Ransomware attacks, social engineering, and other computer attacks. Spoofing attacks can be drastically reduced by using one method of email authentication or possibly even eliminated when firm’s use SPF, DKIM, and DMARC together.
Your firm may already use email authentication.
It’s fairly simple to determine if your firm is using email authentication, but there is a significant difference in the approach firms take to supporting email. Therefore, the following section is divided into two parts, firms that have a custom email domain and those that do not have a custom email domain.
An email domain is the part of an email address that comes after the @ symbol in an email address. A custom email domain is typically a domain owned by the firm, such as mikel@bigdatainsure.com. A standard email domain is owned by the email service provider, such as genericemail@gmail.com . Most firms use a custom email domain to as part of the branding strategy, but many smaller firms such as sole practitioners rely on standard email addresses in the interest of cost and efficiency. As such, we’ve split the material below according to firms that do and firms that do not have custom email domains.
If you don’t have a custom email domain for your firm:
If your firm uses Office 365 or Google Workspaces and you are not using a custom email domain, then you don’t need to do anything else. Both Office 365 and Google Workspaces include email authentication automatically for email (without custom domains) as a default option.
If you do have a custom email domain for your firm:
If you are using Office 365 or Google Workspaces and you have a custom email domain, then you probably have some type of email authentication. When firms initially set up their custom email domains in Office 365 or Google Workspaces, a generic Microsoft or Google DKIM key is included as a default option. The generic Microsoft or Google DKIM key isn’t the gold standard, and both providers recommend that firms set up firm specific DKIM keys and deploy additional email authentication. The best solutions involve a combination of SPF, DKIM and DMARC, a generic Microsoft or Google DKIM key is considerably better than not using any email authentication. If you don’t know if your firm is using email authentication or if you would like to know what kind of email authentication your firm is using then you can check to see what type of email authentication your firm is using (if any) by clicking on the following links:
SPF – https://www.mimecast.com/products/dmarc-analyzer/spf-record-check/
DKIM – https://www.mimecast.com/products/dmarc-analyzer/dkim-check/
DMARC – https://www.mimecast.com/products/dmarc-analyzer/dmarc-check/
If you determine that your firm is not using any email authentication, it’s relatively easy to implement and it’s free to add in Office 365 and Google Workspace. We’ve provided links to implementation instructions for SPF, DKIM, and DMARC below for Office 365 and Google Workspace.
How to Implement Email Authentication in Microsoft Office 365
SPF: https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/set-up-spf-in-office-365-to-help-prevent-spoofing?view=o365-worldwide
DKIM: https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/use-dkim-to-validate-outbound-email?view=o365-worldwide
DMARC: https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/use-dmarc-to-validate-email?view=o365-worldwide
How to Implement Email Authentication in Google Workspace
SPF: https://support.google.com/a/answer/33786?hl=en
DKIM: https://support.google.com/a/answer/180504?hl=en
DMARC: https://support.google.com/a/answer/2466563?hl=en
Have you disables the Remote Desktop Protocol (RDP) on all of your computer networks endpoints and servers?
What is Remote Desktop Protocol (“RDP”)?
RDP is a very popular tool for remote access to Windows machines. The Windows Remote Desktop Connection tool gives users the ability to connect remotely to a Windows PC or server over the Internet or on a local network, giving them full access to the applications, data, and files on it as well as anything else the device has access to. In practice, Windows Remote Desktop typically allows employees to access their work computer remotely from a different computer. RDP is currently the most popular method firm’s use to support work at home employees and it skyrocketed in popularity at the beginning of the Covid-19 lockdown in March 2020.
Many people confuse cloud computing with remote desktop access because they are both popular solutions for a remote workforce, but they are different. In cloud computing, many users can access specified files and applications stored in the cloud. Cloud users are typically subject to stricter authentication mechanisms to control usage and access to data. By contrast, remote desktop software permits a limited number of users access an entire PC or server, typically at the firm’s offices, and all of the files, applications, and data related to that machine. Users who have remote access to a machine usually get access to anything that the machine can access.
What are endpoints?
In computer networking, the term “endpoint” is most commonly used to describe a remote computing device that communicates with a computer network to which it is connected. A few examples of endpoints include the following:
- Desktop and Laptop computers;
- Smartphones and Tablet computers;
- Servers;
- Workstations; and
- Internet-of-things (IoT) devices.
Since endpoints exist outside the firm’s firewall, they are extremely vulnerable points of entry into your firm’s computer network, which threat actors commonly use to launch cyber-attacks or to access the high-value assets and information on your computer network. Endpoints are commonly targeted by threat actors to exploit vulnerabilities, launch Ransomware attacks, or execute malicious code.
Why do open RDP ports a put your firm at risk for Ransomware attacks?
In order to permit RDP access, the host machine must open an access port through the firewall, which is usually port 3389 for RDP. Unfortunately, threat actors also know that firms must open port 3389 to enable RDP access, so once you’ve opened up the RDP port on the firm’s firewall, threat actors can easily find the extremely vulnerable open ports at your firm using automated scanning tools. Once an improperly secured open RDP port is found, the door is wide open for threat actors to launch a variety of attacks including malware, brute force, or targeted Ransomware attacks resulting in catastrophic losses.
Open RDP ports have been a problem for a long time now. In September of 2017, the number of open RDP ports was calculated at 4,500,000 worldwide. Many of those 4,500,000 RDP ports were deployed by professionals after careful planning for security, so threat actors preying on RDP vulnerabilities had to be highly skilled or were forced to work hard to find unsecured or improperly secured RDP ports. The FBI issued a warning in September of 2018 warning companies of the dangers of leaving exposed RDP endpoints online. In that report the FBI noted a significant rise in the number of open RDP ports since 2016 and numerous information security experts issued follow on press releases warning of the rise of criminal syndicates such as using and selling Ransomware specifically designed to be deployed by RDP access and many experts also noted that exchanges such as xDedic were forming to buy and sell hacked RDP endpoints.
The situation changed dramatically during the rush to enable millions of employees to work from home in response to the COVID-19 pandemic. According to early estimates, more than 10 million new RDP servers were exposed to the Internet before the end of April 2020. Unfortunately, many firms didn’t have the time to take RDP security into consideration, so many firms opened the RDP ports in their firewalls allowing remote workers with unfettered access to the firm’s secrets without security measures. It only took a few months of automated scanning before the threat actors began to realize there was a massive increase in the number of new unsecured RDP targets. Shortly thereafter, in July of 2020 the Ransomware feeding frenzy began. The number of Ransomware attacks tripled between March and April alone and the volume of successful attacks became so high that threat actors began bumping into each other during their criminal adventures. By the end of August 2020, some SafeLaw policyholders were being extorted by multiple extortionists at the same time and by the end of 2020 Ransomware attacks had increased by over 700%.
Of all successful Ransomware attacks on SafeLaw policyholders, open RDP ports were the leading cause of all cyber claims in 2020 (not just Ransomware). Furthermore, open RDP ports were used by threat actors in over 90% of all Ransomware claims in 2020. RDP is “the” pathway of choice into your firm’s computer system and unsecured RDP is an open invitation to threat actors. For the sake of simplicity, think of RDP as the low hanging fruit of the hacking world.
How do I know if my firm’s RDP ports are open?
If you have dedicated IT personnel or rely on an outsourced service provider, they can determine if the RDP ports in your firm’s computer network are open or closed. If, however, you don’t have access to an IT resource and/or are not IT inclined, then you can try a simple tool to automatically check the open ports on each machine. One example of a tool that will check the ports on your computer is as follows in the link below:
https://portchecker.co/canyouseeme
How do I disable my firm’s open RDP ports?
The easiest way to disable the RDP ports at your firm is with help from dedicated IT personnel or outsourced IT resources. If you don’t have access to IT resources, disabling RDP is relatively simple. For instructions for disabling RDP on a computers with Microsoft Windows operating systems, please review one of the following links:
https://www.laptopmag.com/articles/disable-remote-desktop
https://www.cisecurity.org/white-papers/intel-insights-how-to-disable-remote-desktop-protocol/
There are a variety of tools to help support a remote workforce without relying on RDP. Smaller firms without significant IT resources should consider a simple cost-effective solution that incorporates a secure connection and allows you to disable the RDP ports to help minimize your risk from working remotely. A few popular alternatives to RDP ports, which are frequently used by small firms follows below:
What is multi-factor authentication and how does it help reduce the risks of RDP access?
RDP is without a doubt a useful tool for firms with remote workers, and for the foreseeable future nearly every firm will have remote workers. For most firms, disabling RDP access is not an acceptable solution, but neither is allowing unsecured RDP access. A better option for most firms is to secure the RDP ports with multi-factor authentication (“MFA”). With MFA properly employed for RDP access, open RDP ports can be reasonably safe. MFA software verifies the legitimacy of authorized users by requiring users to submit two or more pieces of evidence, usually a combination of something only the authorized user knows such as a password, and:
- something only the authorized user has (like a security token or a key); or
- something the user is (such as a physical characteristic like a fingerprint or retina pattern); OR
- somewhere the user is (such as a connection to a specific computer network using a GPS signal).
Multi-factor authentication eliminates many of the problems associated with usernames and password solutions, which are vulnerable to brute force attacks and can be stolen by third parties. Ultimately, MFA provides a reliable authentication method that protects the firm from unauthorized users trying to access the firm’s computer network and company secrets. In addition, MFA is cost effective and Microsoft includes MFA at no additional charge on Office 365 and Azure services. Likewise, Google Workspaces also includes multi-factor authentication at no additional charge.
Do you encrypt all sensitive and confidential information stored on your computer network and sent externally by email?
What is encryption?
Encryption is a complicated subject, but it’s an essential part of protecting your firm’s sensitive data. Conceptually, encryption is a method of scrambling readable data into an unintelligible format, called “cipher text”, so it can only be read by authorized parties that possess the secret password known as a “decryption key” or just “key” to unscramble the cipher text back into readable data. In the context of computer data, the purpose of encryption is to protect confidentiality and privacy of data when it is stored on computer systems or transmitted through a computer network such as the Internet.
There are two main methods of encryption, symmetric encryption and asymmetric encryption. Symmetric encryption is the simplest of the two. Symmetric encryption is executed using only one secret password known as a “cryptographic key” or just “key” that is possessed by the sending and receiving parties. The key is applied by the sender to encrypt the information and the receiver uses the same key to decrypt the information. Asymmetric encryption, which is also known as “public key encryption”, is more complex because it incorporates two separate but related keys for data security, one key to encrypt data, and a different key to decrypt data. These keys are called a “public key” and a “private key” respectively. The public key, which is shared among users, is used to encrypt the data and the private key known only to the owner is used to decrypt the data. Although the use of two keys makes asymmetric encryption more complex, the data security provided by asymmetric encryption significantly is significantly stronger than symmetric encryption.
There are also several different types of encryption for computer hardware, software, and online services like email. The type of encryption applicable any given situation will generally be tied to the state of the data you’re trying to protect. There are three states of data, which are data “at rest”, data “in use”, and data “in transit”. Data-at-rest is data that is not actively being used or transmitted anywhere, such as data stored on a hard drive, laptop, flash drive, or tape backup. Data that is in transit is being transmitted from one location to another through a network or over the Internet. Data is in use whenever it is not in transit or being stored passively, but is being processed by one or more applications, including data that is in the process of being generated, viewed, changed or erased. In most situations, data can be encrypted while it is at rest and in transit, but it is usually impractical data that is in use due to technological limitations. With that in mind, we’ve described a few types of encryption available to protect data-at-rest and data-in-transit in the bullet points below.
Data-At-Rest Encryption
- File Level – File level encryption is as simple as the name suggests. It only encrypts the files and folders that you specify, but not the entire disk. File level encryption is better than no encryption at all, but it’s not considered appropriate for firms that store a significant amount of sensitive information.
- Volume – Volume encryption protects a specific section the disk, which is defined as a partition or “volume”, but it protect the entire disk. That said, volume encryption does have some significant advantages over full-disk encryption. Volume has unique encryption and password for each protected volume, whereas full disk encryption uses one password for all data stored on the disk. If that password is exposed the entire disk is at risk. In addition, volume encryption protects any volume not in use, but full disk encryption leaves all data on the disk exposed once the machine is active and the data won’t be re-encrypted until the machine is powered off.
- Full-disk – Full-disk is considered the most complete form of computer encryption. With full disk encryption, the operating system, applications, and all files, folders, and volumes are encrypted. Full-disk encryption is useful for preventing data breaches because nothing can be accessed on the disk without the password. This is especially important for situations involving lost laptops and other portable devices.
Data-in-transit Encryption
- End-To-End – End-to-end encryption ensures that the data stays encrypted from the time it is first sent until it reaches it’s final destination. When a message is protected by end-to-end encryption, only the sender and recipient can read it. Currently, end-to-end encryption is considered the most secure way to transfer data.
- Encryption-In-Transit – Encryption-in-transit is an older encryption protocol that keeps the information encrypted between the device and the service provider only. In summary, messages are encrypted on the sender’s side, then delivered to the server and decrypted, then re-encrypted, and then delivered to the recipient and decrypted again. Encryption-in-transit protects information during the transmission from the sender to the server, but once it arrives at the server it is decrypted and vulnerable to data breaches and man-in-the-middle attacks.
Why is encryption important?
Data security is especially important to any business that handles private or confidential information, especially law firms. The sensitive nature of data collected, created, stored, and transmitted by law firms makes it an attractive target for threat actors. Encryption was specifically created to keep data secure and is excellent last line of defense when all else has failed. Encryption is a cheap and easy way to reduce the risk of confidentiality breaches or breaches of attorney client privilege and it can even provide your firm with a layer of protection from regulators in some cases.
Many businesses, including law firms, tend to build strong outer defenses with firewalls to prevent threats from getting into the firm’s computer system, which is great, but it is only a part of a successful strategy. It is also important to consider what happens when an attack breaks through the firm’s outer defenses or what happens to the firm’s sensitive data when it is outside the firewall. Depending on how it is used, encryption can protect your firm’s data from a wide range of different threats including threats inside and outside the firewalls. Just a few examples of situations where encryption can help include the following:
- Physical Theft: If your computer or portable device is stolen, encryption at-rest will prevent the threat actor from being immediately able to access your data, which should provide the firm with a reasonable amount of time to execute countermeasures such as tracking or remotely wiping the stolen device.
- Unauthorized Access: Encryption ensures that communications are only viewed by the intended recipient by preventing threat actors and other unauthorized parties from intercepting and reading sensitive data. Likewise, encryption helps ensure that data-at-rest can only be accessed by the rightful data owner. For example, if the firm’s computers are hacked, encryption will prevent the threat actor immediately accessing the firm’s data, giving the firm time to respond and minimize the damage.
- Tampering: Encryption also helps secure the integrity of data transmitted across networks or the Internet, ensuring that what the recipient receives has not been tampered with along the way. For example, many firm’s have been victimized by “man-in-the middle” aka “on-path” attacks in which a threat actor intercepts communications between two parties or devices to eavesdrop, collect data, or modify the communications between the two parties for nefarious purposes.
- Human Error: To the surprise of almost no one, human error is consistently a top cause of data breaches. No amount of training and education will totally eliminate mistakes, so we must accept that human error is a constant threat to the firm’s security and ensure that measures are in place to protect the firm when mistakes occur. For example, if someone from the firm sent a confidential email to the wrong person, encryption would prevent the recipient from reading the data contained within the email. Likewise, encryption would protect the firm’s data in the event a mistake is while assigning permissions and unintentionally granting to unauthorized users access to confidential files/folders/data they should not have access to.
- Regulatory, Professional & Contractual Violations: For the reasons listed above, there are numerous data security and privacy regulations, professional rules, and contractual requirements that mandate data encryption. Furthermore, data that is encrypted is protected by safe harbor provisions under many privacy and security regulations, which could easily be the difference between a disaster and a catastrophe.
Your firm may already use encryption.
Some of the software, email services, and mobile devices available today include encryption. In some cases, the encryption is on by default and in other cases, it must be turned on. For example, if you use Microsoft Office 365, encryption is turned on by default and encrypts your firm’s content while it is “at rest” (stored on your computer) and “in transit” (transmitted by email). Likewise, Windows 10 has BitLocker encryption built-in for data-at-rest, but it must be turned on. Google also encrypts data-in-transit for Gmail and Google Workspace email as well as data-at-rest for Google Workspaces business packages.
Encryption as a standard feature isn’t just limited to operating systems, email, and office suites. Several major practice management software providers such as Clio, Practice Panther, Smokeball, and MyCase all include encryption.
How to implement encryption.
Before you implement an encryption strategy at your firm, it’s important to decide what to encrypt first. There is no single universal standard for encrypting all data, everywhere, and all the time, but taking stock of the firm’s sensitive data and where it is stored is a great starting point. Once you’ve zeroed in on what data you want to protect, then it’s time to start thinking about the best way to protect the data throughout its lifecycle including when it is at rest and when it is in transit.
For many small firms, encrypting the firm’s data while it is stored isn’t especially difficult relative ease. Many popular office productivity software and email services like Office 365 and Google Workspaces have built in encryption built-in and “on” by default in some cases. Likewise, both Windows 10 and the latest MAC OS have built-in encryption also, but it needs to be switched on in most cases. Thankfully, turning on encryption is usually very simple. For example, the BitLocker encryption software built into Windows 10 Machines can be turned on in a few minutes. Please see the following link for instructions.
Software created specifically for law firms, such as practice management software also frequently includes encryption. Providers such as Clio, Practice Panther, Smokeball, and MyCase all include encryption. It may, however, need to be turned on before it is active.
Lastly, many of the popular email providers include encryption as a standard feature. It may need to be turned on, but it’s easy to do. Please see the following like for instructions on sending encrypted email in Outlook, GMAIL, and Mac Mail.
Are administrative privileges restricted to specific users on your computer network?
What are administrative privileges?
In the context of computers, user privileges are the rights granted to one or more users that operate a computer. Such rights may include:
- access to specified system resources such as data files and folders, applications, or storage;
- the type of access users have to resources, such as read-only access or read/write access; and
- permission to make changes in the computer, use certain system commands, and install, disable or remove software.
Administrative privileges provides the user with access to all system resources and permission to make any changes to the computer system. In short, administrative privileges give the user complete control over the computer system.
Restricting administrative privileges is the practice of only enabling the specific privileges needed by an employee to carry out their daily work functions and duties.
Why is it important to restrict administrative access to your computer network?
All computers have system files that are required for the computer system to work properly. If system files are changed incorrectly, part or all of the computer system could become inoperable. Likewise, threat actors frequently attempt to install malicious code such as ransomware into computer systems and/or disable protections such as firewalls.
Restricting administrative privileges is critically important because it minimizes the number of users that can make changes to critical files and systems or delete/install new programs. Users that lack administrative privileges cannot change important system files, disable antivirus or firewall software, and cannot install malware or ransomware. Therefore, limiting the number of users with administrative privileges, dramatically reduces the risk of ransomware, malware and data breaches.
According to a 2016 report issued by Forrester Research, 80% of all data breaches involved the use of privileged credentials in some manner. A similar study in 2019 by Centify stated that the percentage data breaches that involved the use of privileged credentials was 74%.
How can you restrict administrative privileges?
Whether a firm is a solo practitioner or on the Am Law 100 list, the main goal of restricting administrative privileges is to give each user just the permissions needed to perform their work duties. That part sounds simple enough if you’re a solo practitioner, but for firms with more than a few employees, successfully restricting privileges without harming productivity requires that restricting privileges be an ongoing process. With that in mind, we’ve outlined a basic process for restricting privileges:
- Identify the business processes and individual tasks that require administrative privileges;
- Identify the staff that perform those tasks that require administrative privileges;
- Create separate attributable accounts for staff members with administrative privileges;
- Track any changes in accounts with administrative access and audit usage periodically; and
- Revalidate staff members requirements to have administrative privileges at regular intervals and when triggering events occur, such as when a staff member with administrative privileges leaves the firm.
If you are at a very small firm and do everything yourself, the process listed above probably sounds like overkill. Thankfully, there is a simple, but effective approach that smaller firms can use to restrict administrative privileges. Experts recommend that administrative privileges are limited to 1-2 people and everyone uses non-administrator accounts for the everyday work of practicing law. The administrator accounts are only used for patching and adding software as needed. With this in mind, the link below will provide you with instruction for adding a non-administrator account to any Windows 10 device:
Additional resources to protect your firm
While we have covered the requirements of the application, we wanted to provide additional resources you can use to protect your company and yourself from the increased risk of Malware and Ransomware.
AntiVirus
AntiVirus Software while not perfect, can help detect malware before it happens. There are a variety of anti-virus softwares available to use that we have linked to below:
https://us.norton.com/products/norton-360-antivirus-plus?inid=nortoncom_nav_norton-360-antivirus-plus_homepage:home
https://www.mcafee.com/en-us/antivirus/smb.html
https://www.avira.com/en/for-business
https://usa.kaspersky.com/small-business-security
VPN
With everyone working from home, a VPN is useful to help protect the connection between your home computer and the network at your law firm. Below is an example of a large VPN provider that makes it easy to set up on your home computers and even some devices.
Each layer of protection makes it harder for the threat actors to target and take advantage of you. And while the internet has made it easier to target small businesses, software has gotten extremely cheap to protect you against these attacks.
